Introduction:
(Note: If you know how DSL works, you can jump to the next section!)
Most of the internet users nowadays are using DSL connections. DSL stands for Digital Subscriber Line which provides internet over telephone lines. DSL uses ADSL Routers or ADSL Modems. Here is a layman diagram of how DSL works:

Whenever a user turns on their DSL modem, they are connected to the DSLAM which is usually placed inside ISP Exchange. Each DSLAM has the capacity to connect with thousands of DSL users. In above image, it looks like a small box but actually it is much bigger:

DSLAM is responsible for checking the condition of telephone line and assures that a stable connection can be maintained. It also holds some properties for each telephone line. The Download and Upload Rate you see in your modem status page are also set by DSLAM. Once the DSLAM connection is established, the DSL light on some modems is turned on.

Now the modem sends Internet Access request to the BRAS server. This request contains the DSL username and password which is saved in the DSL modem settings. The login is usually set by the lineman when they install a new DSL connection. The BRAS server is directly connected with the central RADIUS server which contains login information of all DSL users. The RADIUS server also contains a list of IP Addresses which are not used by others. If the login sent by modem is valid, RADIUS server responds with one IP Address from the IP Address list. Once the modem receives the IP Address, an internet connection is established and the internet light on modem is turned on:

That was some lengthy introduction about DSL and its working for non-technical people!
How to Hack:
After reading the above introduction we know that each DSL connection is assigned a unique Public IP address from a list. This list is basically a range of IP Addresses which is assigned to the ISP by the RIR. We can check our IP Address from here: http://myip.counterstrike.com.pk/. I assume my IP Address is 66.150.150.10. The IP Address we see is basically the IP Address assigned to our modem. What will happen if we change the last part of our IP Address and enter 66.150.150.11 it in web browser?

Oh. It looks like that IP Address does not belong to any DSL user. Lets try 66.150.150.11:

(Keep increasing the last number of IP Address until you hit a login page. Don’t give up too soon!)
Looks like we have reached the login page of another DSL users’s modem. The default login for most modems is admin:admin. More default logins are given in next section. Once we login successfully, we have full control over that modem.
For example:
-
We can steal their DSL login and use their bandwidth:
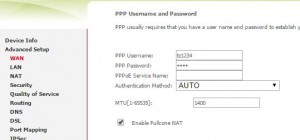
-
Change their DNS Servers and hijack their DNS Requests:
-
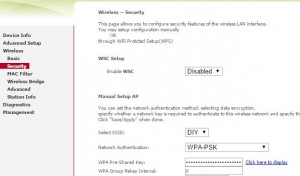
Steal their Wi-Fi keys:

-
Enable DMZ to remotely access internal LAN computers:

-
Replace ACS with our own for remote configuration of modem:
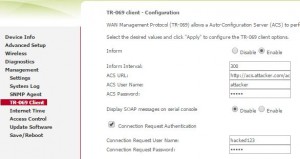
-
Replace modem’s firmware with our own backdoored firmware:
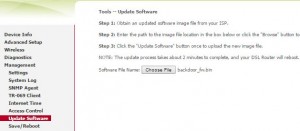
As you can see, we can do pretty much anything we want with that DSL Router we just owned.
How to Secure:
Now that we have learned about the various tricks to exploit the router, lets go through the different ways to secure it:
-
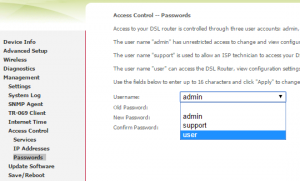
Change Default Router Configuration Password:
If you have installed a new DSL connection, chances are that your login and password combination is one of the following default logins:
admin:admin
support:support
user:user
admin:ISP NAME
admin:LAST 5 HEX CHARACTERS OF MODEM MAC ADDRESS+1
Always use a strong password that does not include dictionary words.
Some modems have multiple login accounts so make sure you have changed passwords for all of them:
-
Change Default DSL Connection Password:
Call your ISP helpline and ask them to change your DSL or Broadband or PPP account password.
If you do not change it, someone else might use it and you will be billed for their download usage.
-
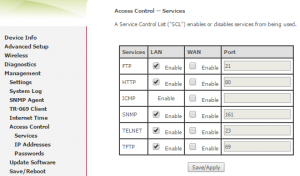
Disable Remote Access to Modem:
This is to make sure no one can connect to your router from outside your network.
-
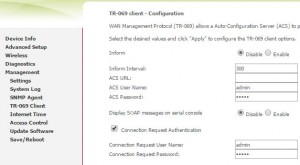
Disable TR-069 Client:
If you know how to configure your router, you don’t need your ISP to remotely access your router.
So you can simply disable it.
-
Use Strong Wi-FI Password:
Always use a strong WPA/PSK key for password. If the attacker is on LAN, means they have your Wi-Fi password, they can easily sniff your router credentials using MITM on your local network.
-
Be Smart:
If you connect to your Wi-Fi network and the browser opens a page asking for your Wi-Fi password, beware! Someone is trying to hack your Wi-Fi password using Wi-Fi Phishing. This is a new technique and it cannot be prevented directly. All you can do is educate your friends and family about how this works so they should be cautious about these attacks.
If you follow the above steps, no one can break in to your router remotely or locally.
Conclusion:
The sole purpose of writing this post was to spread awareness about security and to educate the internet users and the ISP operators about the different threats they are exposed to.
So if you suspect that your router might be vulnerable, now is the right time to secure it.
Better safe than sorry!